
In this era of ruthless competition and advanced corporate spy activities, it is only important that business information is secured. TSCM services and corporate debugging have all become requisite protective measures whenever Indian corporates need to achieve security of its secret information and communications. Technical Surveillance Counter-Measures (TSCM) are those technical measures to sweep undetected electronic bugging devices, including minute wireless transmitters to hidden cameras, and disarm the threats.
Organizations are now actively undertaking bug sweeping and electronic surveillance detection as it helps prevent data theft and eavesdropping especially in India. A brief discussion behind why the services is important and what can be expected when investing in the services of a professional bug sweeping business in India is provided below:
Main Highlights & An Overview
- Increase Corporate Espionage: Companies are being threatened with Corporate Espionage such as competitors and other unfriendly parties introducing spy devices with the intention of stealing the business secrets.
- Full Debugging Services: The Pro TSCM Services do employ the usage of sophisticated RF detectors, covert camera detectors, and physical searches to get any bug in offices.
- PAN-India Coverage: The best debugging experts are available in India such as ADA across the length and breadth of the country, Delhi, Mumbai, and even in the lower tier cities so that not even a single office lies out of reach of security.
- Proven & Stealthy: A trained TSCM team uses military-grade tools and is highly discreet (work is typically done off-hours) requiring no intrusion in the workplace or process.
In this page, the role of TSCM to corporates, the full range of service responses, the pan-India scope and procedure of ADA and the frequently asked questions regarding the detection of spy equipment in office space and counter-surveillance are explored. You will, by the end, know how professional bug sweeping solutions make your conversations in business and business data actually secret.
Importance of TSCM Services in Indian Corporates
Increase in Corporate Spying
There has been a rapid increase in the cases of corporate espionage in the current competitive world. Global conglomerates and even the use of Indian companies are at risk of competition and even rogue insiders that seek confidential information. Massive spying, especially involving the sale of classified government documents to energy corporations, has made national news in India, such as when Delhi Police in 2015 broke up what is described as one of the largest corporate espionage rackets in the country after stealing and selling classified government documents.
As a global average, corporate spying is believed to cost companies stratospheric amounts of money; estimates go to above 2.24 trillion dollars annually as a result of corporate espionage. These statistics highlight that this threat of espionage is not farfetched but real. Companies which disregard it face the possibility of massive losses and bad names. The volume of the spying activity has increased to such an extent that companies must actively protect their confidential information and communications.
“Our team has uncovered multiple threats through proactive corporate espionage investigations, helping Indian firms safeguard trade secrets, boardroom discussions, and sensitive IP from internal and external breaches.”
Information Theft, Eavesdropping and Concealed Monitoring
Data breaches are not only perpetuated by cyber hackers; some are perpetuated by devices planted in the office itself. Tapping phone lines, melted microphones, and cameras disguised as clock eyes are all weapons of the corporate spy. Conference phones, power strips or even such harmless items as pens and wall clocks might be installed with tiny listening bugs. These devices are installed in confidential meetings, secret discussions, and client information and result in grave data loss. Indeed, in case there is some small device that is placed in a conference room or cubicle, there are chances that the employees are unwillingly sharing confidential discussions and intellectual property with eavesdroppers. Such espionage will not be noticed until months pass without it being detected particularly without active electronic surveillance.
The outcome is traded secrets that become leaked, competitive advantage that is lost, and privacy that is infringed. Any wiretapping or any surveillance camera is a lethal blow to the integrity of any company and therefore professional identification and elimination of such surveillance devices is of utmost importance.
Weaknesses in Boardrooms & Server Rooms
Facilities such as high-level meeting rooms and IT centres in offices are usually the lowest security links. The directors and executives have confidential meetings in the boardroom which makes it one of the best targets of spies. Covert installation of listening devices can be done by competitors or malicious insiders by fixing monitors in conference phones, ceiling tiles, projectors or right down in the wall sockets, transforming a closed-door strategy meeting into an open book.
Similarly, server rooms where there are critical networks and data can also be bugged with rogue bugging devices even in the event the intruder has access to it even in a matter of a few seconds. A small hardware recorder or an undercover Wi-Fi transmitter can be inserted into network racks or cable conduits, without any notice it will steal the data. Without special sweeps, these concealed threats may not be identified. Periodic sweeps and debugging of conference rooms (close inspections of conference rooms to ensure that the rooms have no bugs) and regular boardroom sweeps (electronic bug checks of boardrooms) are therefore necessary in addition to close checks of server closets.
Alternatively, bugs stuck under tables or chip transmitters secretly affixed to equipment have been discovered in even so-called secure installations. Companies can seal off the common portals of corporate espionage by making boardrooms and IT rooms a high-risk area and conduction TSCM sweeps in these locations regularly.
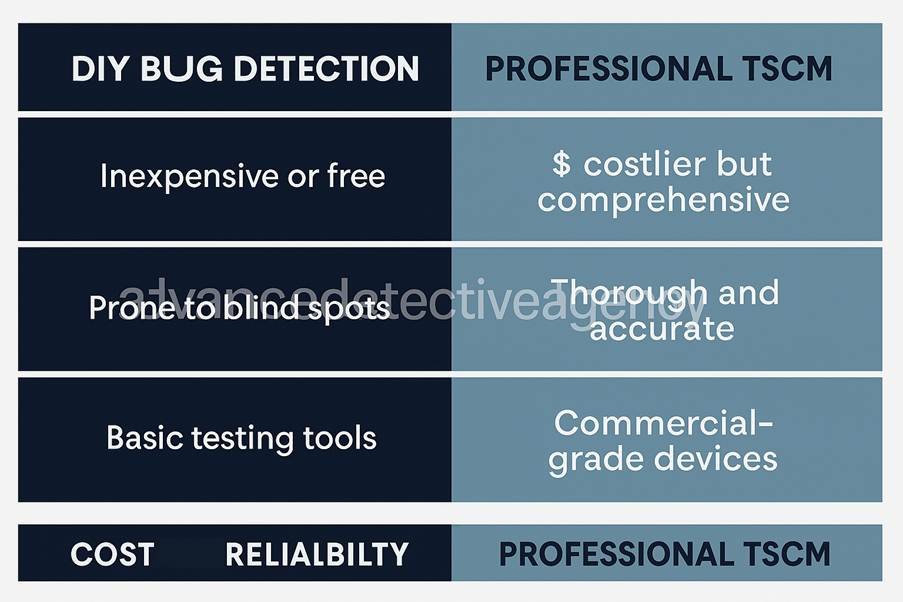
Figure: “DIY Bug Detection vs. Professional TSCM”
Our Offering: End-to-End Corporate Debugging
ADA offers a wide range of corporate TSCM services in India and its services do not leave any stone unturned in regards to detecting and neutralizing the surveillance threats. The company offers debugging services to business and uses state-of-the-art software, which are manned by experienced experts. Notable offerings are:
RF Signal Detection Spectrum Analysis
Listening to tell-belt radio signals is one of the initial moves in any bug sweep operation. The audio or video of many covert listening machines is wireless. The team of ADA uses modern spectrum analyzers and special RF detectors to check the full spectrum in the area of interest. Our RF bug detection services include everyday bands (such as FM, Wi-Fi, GSM) and weird frequencies that may be used by homemade or foreign devices.
This can be done through spectrum analysis (low MHz up to high GHz) hence detecting any suspicious radio signal that could be emitted by the bug. Any device that transmits a signal will be detected by the equipment in the event that it is set up in your boardroom or office. This way depth RF sweep ensures nothing will be overlooked, including a beeping radio bug or a Bluetooth spy camera that was placed in the room with a hidden two-way radio.
Identification of Hidden Camera & Microphone
Not every surveillance device transmits radio signals, some leave a recording locally or are transmitting only periodically. That is why experts of the ADA carry out thorough detection of hidden cameras and microphones which might be hidden somewhere in the surroundings. They search every dark corner with specialized gear such as lens detectors (they detect the glint of the lens that cameras have) and non-linear junction detectors (NLJDs that detect the electronic circuitry of the bug). We inspect boardrooms, offices, washrooms even decor items to check whether there are pinhole cameras, hidden CCTV units or microphones fitted on furniture.
The office environment should be watched keenly and get the right equipment to detect the spy devices. The technicians do a thorough search checking in the smoke detectors, air purifiers, electrical outlets which are likely to be used as hiding places of any unauthorized optics and wires. Any device that is found to be susceptive is reported, e.g. a small camera found on top of a flowerpot; a microphone under a table is immediately reported and removed. With the full-feature design, our debugging experts do not leave any sightless camera or microphone unnoticed.
“Our specialists are trained in advanced hidden camera detection services using RF, infrared, and thermal imaging to uncover even the most covert surveillance threats.”
GPS Bug Detection, Wi-Fi, and GSM
Current equipment used to eavesdrop tends to make use of common means of communication such as local Wi-Fi networks, or cellular SIM cards. ADA technical counter-surveillance services in India include sniffing out not just bugs deployed over Wi-Fi, GSM mobile networks, or GPS signals. The team will be able to spot rogue Wi-Fi access points or unknown Wi-Fi devices operating in your office – such as a spy camera transmitting video over Wi-Fi, or a bug sending off uploads over a hotspot. We also sweep cellular frequencies in search of the signature bursts of GSM-based bugs.
More sophisticated audio bugs have SIM cards and intermittently transmit call or text data and transcribed overheard conversations; the bug locators can even locate these rogue cellular transmitters. We also have GPS bug detection that will identify any trackers on any vehicles or assets of the company. The engineers use spectrum analyzers and hand-held detector units to hunt down the GPS-tracking device by their characteristic ping (usually relayed via SMS or a radio beacon) sound. That is, not only do we detect Wi-Fi bugs, GSM bugs, GPS bugs in every sweep, but we also make sure none of the digital spy gadgets evade our grasp; be it a rogue wireless recording device on your network or a GPS tag lurking in a company vehicle.
Thermal and Physical Inspections
Physical examination of the premises should be a great essence of the bug weeding process. Using painstaking procedures, TSCM experts of ADA examine thoroughly every possible hiding place under the desk, inside ceiling panels, behind wall fixtures, in phone handsets, etc. to detect any hidden equipment or other suspicious wiring. The team are also using thermal imaging devices to sweep through any heat signature detectable as a sign of an active electronic device that may be embedded identifying walls or equipments. It implies that even a powered-on camera or transmitter that is out of sight will be detected since all emit a little heat.
Also, the telephone lines and network cables are scrutinized to make sure that they have neither been tapped nor do they have alterations. The integration of a keen-eyed physical inspection with state-of-the-art thermal radiances enables the force to detect bugs that otherwise could not be noticed by standard observation. Various devices detected in this inspection process are recorded and physically taken off site immediately eradicating its threat.

Where We Operate – PAN India Bug Sweeping Coverage
ADA is Pan-Indian. The company being the number one bug sweeping company in India is able to be deployed swiftly to any city or location. We have established a wide network of bug detecting specialists throughout India and have a wide range of coverage with quick on-site assistance anywhere.
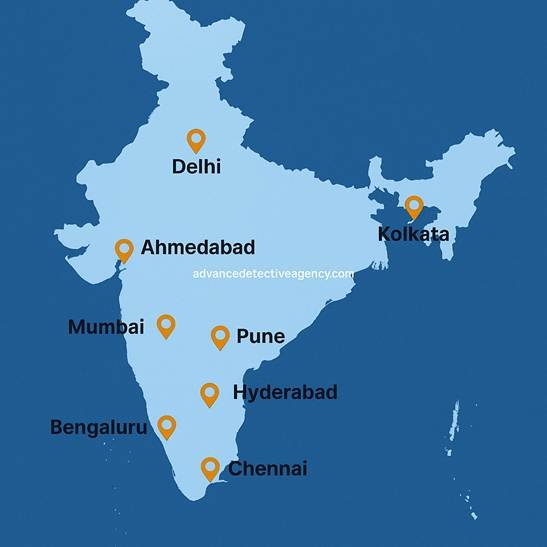
Delhi, Mumbai, Bengaluru, Hyderabad
The services of ADA are well covered in India, the largest commercial centers. We have dedicated teams on call in Delhi (and NCR region of Gurugram and Noida), Mumbai, Bengaluru and Hyderabad. These metros have an endless number of corporate headquarters, financial city centers, and technological parks – all of which are near valid espionage targets. We have local offices in every city, and we can be in a Delhi boardroom or a Bengaluru technology campus in a short time. With our team members being well-seasoned in their particular cities; we have sweeps in Mumbai tall buildings and Hyderabad IT parks. Whether your office is situated in a Connaught Place tower or a Bangalore tech park, ADA has delivered discreet, prompt TSCM in all the major metros.
“We offer swift and discreet bug sweeping in Delhi for corporate offices, boardrooms, and executive residences, covering all zones including South Delhi, Noida, and Gurugram.”
Pune, Ahmedabad, Kolkata, Chennai
Other major business centres are served by ADA outside the top four cities. Our coverage area includes Pune (IT and automotive cluster), Ahmedabad (corporate and industrial center), Kolkata (eastern business capital) and Chennai (manufacturing/technology hub). When necessary, our staff goes to such places and performs comprehensive sweeps of such areas. Whether in a boardroom of the Hinjawadi in Pune or factory of the industrial estate in Ahmedabad, clients get the same expertise of bug sweeping services. TSCM services of the highest quality can therefore be available to companies based not just in the largest metros, but in all the geographies that the pan-India operations of ADA cover.
Tier-II Cities and Industrial Corridors
The coverage of ADA is also in new cities and industrial regions of India. We cover much Tier-II cities Jaipur, Lucknow, and Indore to Kochi and Coimbatore etc where businesses are on an upward trend and require protection. Our scope of interest includes major industrial corridors and special economic zones, such as Gujarat to Tamil Nadu. Wherever and however dispersed your facilities are, we will provide a professional bug sweep wherever and whenever it is needed via our national network.
Our TSCM Sweep Process – Step by Step
The process of debugging is observed with methodical precision and discretion. The mechanism of ADA to sweep is not a single-restricted method that should be tested by numerous years of its functioning; instead, it is a multi-stage shearing system that will not leave a threat unnoticed and do not compromise the confidentiality of clients.
Threat Assessment & Signing NDA
Each contact is initiated by a detailed assessment of situation and formal confidentiality procedures. The specialists at ADA begin by engaging in a consultation to the client and conducting a threat assessment. The team exchanges any kinds of suspicions or recent occurrences (such as unexplained leakage of information or discovery of suspicious objects), as well as high security hotspots such as executive offices, boardrooms or server rooms. This assists in customizing the sweep plan on the basis of the needs of the client. In this preliminary phase, ADA enters into another tight Non-Disclosure Agreement (NDA) with client organization as well. The NDA gives the legal assurance to keep all the information of the sweep, and the knowledge of the abduction, to itself.
Clients have the assurance of a worry-free state since the process of sweeping is done with the maximum of secrecy and professionalism. The debugging sweep will normally be planned at a time when it will cause the least interruption, i.e., in most cases, after office hours or during the weekend to ensure the least disruption and not to alert the potential perpetrators. The prerequisite of a successful TSCM operation that has been discreet is the excellent pre-sweep evaluation and the confidentiality, which has been garnered by the NDAs.
On-Location Multi-Layer Debugging
On the date chosen, ADA team makes an on-site sweep with different methods at once. The first stage, experts carry out an electronic scan: they wave spectrum analyzers and RF detectors into the field to see what was transmitting. They then are sent NLJD gizmos and other detectors to scan around the environment to track down non-transmitting electronics (such as switched-off bugs). Meanwhile, they conduct a comprehensive physical search, looking through furniture, fixtures, electronics and other objects checking them for possible suspicions or tampering.
This tier system puts into consideration that, whether a bug is currently transmitting or not, it will be identified and disabled, either way. During the process, the technicians have to be discrete (usually working at nigh/after hours) to escape attention. It follows that all illegal devices are detected and disabled on the spot immediately, ensuring the safety of the premises.
Detailed TSCM Audit Report & Recommendations
The last step in our service is analysis and direction. ADA produces a detailed TSCM audit report to the client after completing the sweep. The areas that were swept and the equipment that was used are written down in this written report along with the findings of the sweep. Any surveillance device found is outlined with its type, location, and its likely designation in addition to how it was countered. Even where no bugs are detected, the report outlines any security vulnerabilities detected (like unsecured entry points or bad information-handling mechanisms).
Notably, the audit report will contain recommendations on security enhancement that are specific to the client. Among the measures that can be recommended by the experts at ADA, the following should be mentioned: enhancing physical access controls, periodical preventive sweeps (particularly preceding an important meeting), encrypted communication applications, or teaching personnel to detect spying activity. All findings, as well as the suggestions received, are discussed in simple language with the team of the client so that they are aware of the outcomes and what is being proposed. The consultancy process culminates in delivery of this report and a debriefing session which provides the organization with a concise plan to shore up its counter-surveillance against future attacks.
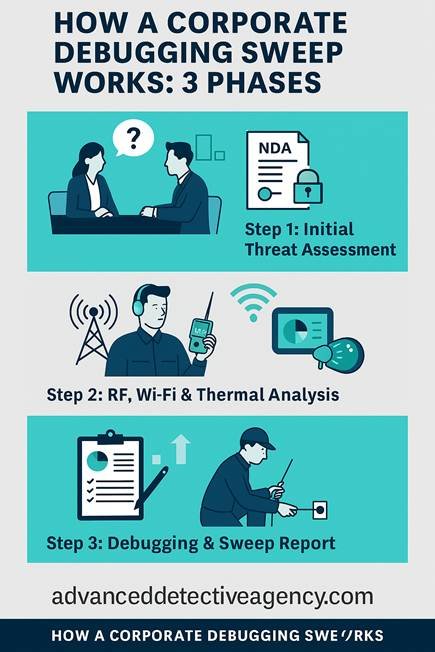
Figure: “How a Corporate Debugging Sweep Works – 3 Phases”
Who needs our TSCM services?
In the contemporary setting, active counter-surveillance is beneficial to multiple industry players and individuals. Cross section of clients ADA provides consultation services against surveillance to the leadership of big corporations, corporate attorney channels, government agencies and in-house research and development departments.
Executives, Directors & CEOs
TSCM is also common among corporate leaders. Strategy discussions, which entail sensitive financial plans, and personnel decisions, may include sensitive topics fit to be discussed by CEOs, board directors and high-ranking executives since competitors or adversaries are likely to want to hear them. one escaping boardroom conversation can kill a merger or reveal a market strategy. To avoid such dangers, most high-ranking managers in India hire debugging services to have their rooms and meeting areas secure. Frequent searches of the CEO office, meeting room and even company cars allow them to make sure that they are not being spied on by hidden microphones and cameras. TSCM services provide security on the privacy of leadership discussion therefore executives can execute their plans without the fear of espionage and leaks of information.
Law firms, IPO advisors, and M&A advisors
TSCM is also used by professional service firms involved with high-value information. The cause of keeping law firm discussions confidential is vital in cases where a law firm may represent a client in significant business litigation or negotiation, and any information overtly related to a client during discussions must remain extremely confidential lest it leaks out to the other party and negates a whole case. This is the same case with financial advisors dealing with IPOs or mergers and acquisitions (M&A) who are privy to insider information that would be disastrous should it fell in the hands early.
Corporate debugging sweeps are initiated by investment bankers, deal consultants and due diligence teams to lock-down meeting rooms and data rooms in sensitive negotiations. These professionals are available to provide counter-surveillance checks regularly so that negotiations over the contract and other legal procedures, including legal plans and other details of the deal, remain confidential. Any espionage activity in these areas costs – a lost court case or a deal that has fallen through-businesses, in these specialized areas costs untold numerous times all that it costs a business to conduct a preventative bug sweep.)
Government Buildings & Restricted Areas
There is also the necessity of counter-surveillance in sensitive government and public-sector spaces. The ministries, defense departments and the intelligence units in India cannot afford losing any confidential discussions to intercepted devices. Diplomatic or government offices around the world have had incidences of being bugged by adversarial elements and thus proactive sweeps must be undertaken.
TSCM services of ADA have been harnessed to verify that ministerial boardrooms, secretariats, and police headquarters are not equipped with illegal surveillance facilities. The technical sweeps of meeting rooms, offices of top officials, and even official cars give an extra measure of security on top of ordinary security measures. Similarly, sites with restricted access like defense research laboratories and military conference halls may have regular debugging times. TSCM services help to safeguard state secrets and national interests by stopping eavesdropping there where it is important.
IT Parks, R&D Labs and Innovation Units
Innovation and iPhone espionage are companies whose organization depends much on their intellectual property. The IT parks have trade secrets in form of tech firms, biotech R&D labs, automotive design labs and even the startup incubators whose secrets the competitors or foreign agencies can try to get hold of.
TSCM services of ADA can assist these organizations in protecting their innovations. There are times we will conduct a physical clean-up of the development centers and labs to make sure there are not any hidden cameras or where some of these things might be recorded. TSCM envisions protection of patents, formulas, source code and other important intellectual properties by ensuring that no espionage device is installed in development and creative areas where top secrets are determined.
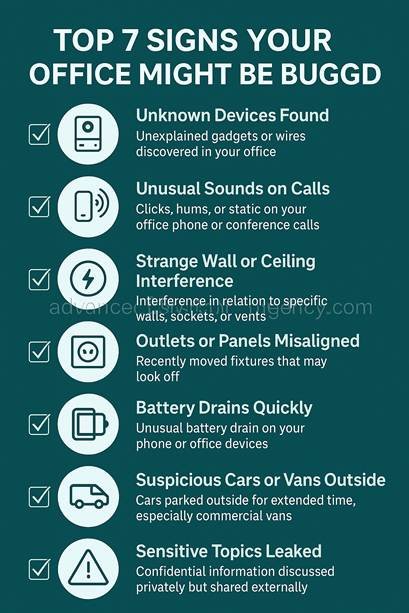
Figure: “Top 7 Signs Your Office Might Be Bugged”
The Advantages of using ADA in Corporate Debugging
With over 2 decades of experience in providing TSCM services, ADA brings in an edged technology and time-tested experience. These have made us stand out and be the professional TSCM cleaning organization of preference used in the Indian corporate isolation debugging services:
Military-Grade Equipment
ADA uses state of the art surveillance detection equipment which is on par with those used by the intelligence agencies. We have a complete line of professional TSCM equipment – ultra wideband spectrum analyzers, high sensitivity RF probes, nonlinear junction detectors (the sniffers of electronics even when a device is in an off state). We also use thermal imagery cameras to detect the heat of devices concealed and high-powered lens finders to locate pinhole cameras. All the equipment is off-beat and is modernized.
The firm never stops updating its equipment to deal with new threats (such as detectors of the latest wireless protocols or microscopic transmitters). This high-quality military equipment provides ADA with a technological advantage. It allows identification of the bugs that would probably be missed by off-the-shelf gadgets. Even more complex equipment will not remain unnoticed under such equipment.
TSCM Engineers with experience
The construction of the quality of its people is another reason to go with ADA. A specialized team of debugging experts is based in India that has relevant experience on every sweep. The TSCM engineers at ADA hold a background in such related fields as electronic security, telecommunications and law enforcement and have a sharp understanding of how a bug may be hidden and where some of these may be found. The training of each team member is stringent on the latest counter-surveillance techniques.
They have experience with hundreds of different spying tricks as they have spent several years in the field and are aware of how to deal with each one. Notably, they screen all personnel in terms of their integrity and professionalism they will be fully discreet in secretive corporate settings. When ADA sweeps, the clients get experience in utilizing bug detecting gurus who have the knowledge on how to locate the needle in the haystack.
Concerted Operations Legality, Ethics and Confidentiality
ADA takes pride in professional conformity. ADA performs all TSCM activities in a legal and highly ethical manner. Our team members obey confidential agreements and powerful code of ethics. They keep secret the sensitive information regarding a client: results are reported only to interested parties and information on a business of a client is never shared with third parties. In essence, the activities of ADA are 100 percent confidential and ethical.
The counter-surveillance services of ADA are something that businesses can use without fearing that their privacy will be infringed upon and that they may move beyond the legal boundary. This trust is reflected in our immaculate record of working in high-security sensitive corporate and government environments.)
20 + Years of Counter-Surveillance
It is not about theory when dealing with counter-surveillance, it is all about experience, and ADA has the best record. Having more than 20 years of experience in this sphere, ADA has resolved numerous corporate bugging cases. The team has managed to handle all kinds of situations, including the simple sweeps of conference rooms, as well as the most sophisticated espionage efforts over the years. The fact that ADA has been in existence ascribes to its performance and credibility- several clients have sought the assistance of the firm in various tasks.
The experience level also implies that our specialists have experienced nearly all spying techniques and understand how to eliminate them. ADA has adapted along with the era and is constantly making upgrades of skills and existing equipment along with the surveillance technology. ADA currently has Pan-India coverage along with several offices and a flawless service quality. Forming a partnership with someone who has 20+ years of experience in counter-espionage knowledge can ensure that businesses can be confident that any shifty bug would be detected and eliminated.
Frequently Asked Questions (FAQs) on Corporate Debugging & TSCM Services
What is corporate debugging and TSCM?
Corporate debugging indicates detecting and getting rid of secret listening gadgets in the corporate area. TSCM (Technical Surveillance Counter-Measures) can mean the methods and services required to detect and defeat such spying devices to guarantee privacy.
In Indian law, is bug sweeping legal?
Yes. It is not a crime to inspect your own premises of any hidden devices in India. Indeed, spying without your permission is not allowed in India, and therefore performing a bug sweep to safeguard your privacy rights is your right and completely legal.
How frequently ought an office to be swept against bugs?
Take an annual TSCM sweep, or just prior to important meetings, if possible. Quarterly sweeps are regularly done by many companies as well as always prior to major events to make sure no devices have been planted.
What does a TSCM audit report contain?
It records everything reported in the sweep. As an illustration, it will clarify any bugs identified (type and location) and security vulnerabilities, and give you recommendations on how you can enhance security of your office against future threats of surveillance.
What is the length of sweep?
It varies according to the size of the location. Normal office sweep can be completed in a few hours, but a multi-floor office or large facility will take all day to go through all the floors and equipment.
Are you able to sweep multi-floor or pan-India stores?
Yes. ADA is capable of managing multiple storey offices and that it has pan-India reach. ADA can also organize a series of TSCM sweeps in several places nationwide to make sure that all the locations of your company are equally secure.
Conclusion – Final Words
To conclude, corporate debugging & TSCM services are a sensible or rather defensive step that any Indian business can take in the current operations environment of high espionage risks. Companies that incorporate services of experts such as ADA will thus keep their sensitive data secret, safe, and beyond the reach of adversaries.
H2: Book Corporate TSCM Services – Pan India Support Available
Secure your boardroom today – schedule a TSCM audit with ADA’s experts.
Confidential, fast, and effective debugging services for businesses across India.
Call / WhatsApp +91-8882732221 or visit advancedetectiveagency.com to book.
